A Very good document that I obtained from Scribd by a student on Classless networks:
- Note: This document is for absolute beginners and may be too simple for others
A Very good document that I obtained from Scribd by a student on Classless networks:
Static IP Routing:
#ip route <ip address> <subnet mask> <next hop ip or exit interface>[d]
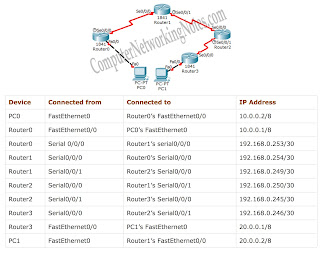
Router0(config)#ip route 20.0.0.0 255.0.0.0 192.168.0.254
Router1(config)#ip route 10.0.0.0 255.0.0.0 192.168.0.253
Router1(config)#ip route 20.0.0.0 255.0.0.0 192.168.0.250
Router2(config)#ip route 10.0.0.0 255.0.0.0 192.168.0.249
Router2(config)#ip route 20.0.0.0 255.0.0.0 192.168.0.246
Router3(config)#ip route 10.0.0.0 255.0.0.0 192.168.0.245[e]
--------------------------------------------------------------------------------------------------------------------------------
--------------------------------------------------------------------------------------------------------------------------------
Loopbacks:
IP Routing:
--------------------------------------------------------------------------------------------------------------------------------
IP Addressing
Note: the (-2) in no. of hosts is because one address is for n/w address and another one is for broadcast address
--------------------------------------------------------------------------------------------------------------------------------
Subnetting:
LAG (Link Aggregation):


Thus, the LAG makes two links appear as one in STP
Note: The physical type (SFP,...) and speeds(10G,...) of all links in a port-channel should be the same.
#int et 17-18
#channel-group mode on //static configuration of link aggregation
Where channelgroupnumber = 1
#show span //we can see the port channel 1 in show spanning-tree
#show int port-Channel 1 (OR) #show port-channel
#tcpdump int po1
DYNAMIC LINK AGGREGATION:
#channel-group mode active //dynamic lacp active
(OR)
#channel-group mode passive //dynamic lacp passive
#lacp rate fast //1 seconds
(OR)
#lacp rate normal //30 seconds
(OR)
In the rate fast timeout configuration, an LACPDU is sent every second. If no response comes from its partner after 3 LACPDUs are sent, a timeout event occurs and the port channel is removed.
(1 Means it has been allocated to the correct link aggregation group, the group has been associated with a compatible aggregator, and the identity of the link aggregation group is consistent with the system ID and operational key information transmitted. If the value is 0, the link is not synchronized .ie. it is currently not in the right aggregation.)
Legacy STP or Common STP:
RSTP:
(Q) Configuring MT701 to MT705.
Mn431 #int et 43
#ip addresss 10.1.10.1/24
MT701 #span mode rstp
#span priority 0 //setting it as root bridge
------------
MT702 #int et 1/1, 1/2, 1/3
#span cost 8000 //If it checks the cost, then, et ¼ will have the lowest cost. Hence, it will become root port
-----
MT702# terminal monitor //use this on the switch where we are going to configure BPDU guard
#show log
MT701 #int et 20
#span bpdufilter enable
MN701 #ping
MT702 #watch diff show int et ⅓ //we see that there is very high broadcast which shows that there is looping
(OR) #watch diff show int et ⅓ counters //this command shows unicast, multicast and broadcasts separately
#int et ⅓
#span bpduguard enable //enabling the BPDU guard
MT701 #int et 20
#no span bpdufilter enable //disabling BPDU filter on port 20 of MT701
MT702 #show int status //we will see that the interface et ⅓ will be shown as error-disabled due to BPDU guard which disables it due to the broadcasts
#show int et ⅓ status error //we can see the reason for the error-disabled- shown as bpduguard
-------
|
MT704 #int et 19 #shutdown #no shutdown |
In another computer, MT704 #watch diff show span \\we can see how fast an port is changing from alternate to root and to original again
MT704 #watch diff show span detail \\we can the number of topology changes and the time |
In another computer, MT704 #tcpdump int et 20 |
------
MT701 #watch diff show mac add //we will see that only the mac addresses on designated ports are cleared. The mac addresses on root port are unaffected.
MT702 #int et1/1
#shut //we will see that the mac table on MT701 is cleared for the interface et 19 (since et 19 is connected to 1/1)
#no shut
-------
MT702 #int et ½
#span guard root
MT704 #span priority 0
//thus, now for MT702, it gets a superior BPDU to a root bridge MT704. But, already it thinks MT701 is the root bridge
MT702 #show span //it shows inconsistent state on et ½ since we have configured root guard. If we had not configured, then, this port would have become root port and MT704 would have become the root bridge.
-------
MT701 #int et23
#span fastport auto
MN431 #ping 10.1.10.2
|
In another computer first type this and watch, MT701 #logging console 7 #logging monitor debugging #terminal monitor //this command displays the debugging and changes on the monitor (no need to use show logging separately)
|
MT701 #int et 23 #shut #no shut
|
//we will see that in debugging, it takes around 20 seconds to move the port to listening port and then to designated port.
MT701 #int et23
#span fastport edge
& repeat the above steps // we will see that the moving only takes 1 second.
--------
ASSIGNMENT QUESTIONS:
Counting to Infinity http://blog.ine.com/wp-content/uploads/2011/11/understanding-stp-rstp-convergence.pdf
Proposal and Agreement
http://blog.ine.com/wp-content/uploads/2011/11/understanding-stp-rstp-convergence.pdf
4) Difference b/w STP and RSTP:
https://cciethebeginning.wordpress.com/2008/11/20/differences-between-stp-and-rstp/
(Q) Configuring MT701 to MT705.
Mn431 #int et 43
#ip addresss 10.1.10.1/24
MT701 #span mode rstp
#span priority 0 //setting it as root bridge
------------
MT702 #int et 1/1, 1/2, 1/3
#span cost 8000 //If it checks the cost, then, et ¼ will have the lowest cost. Hence, it will become root port
-----
MT702# terminal monitor //use this on the switch where we are going to configure BPDU guard
#show log
MT701 #int et 20
#span bpdufilter enable
MN701 #ping
MT702 #watch diff show int et ⅓ //we see that there is very high broadcast which shows that there is looping
(OR) #watch diff show int et ⅓ counters //this command shows unicast, multicast and broadcasts separately
#int et ⅓
#span bpduguard enable //enabling the BPDU guard
MT701 #int et 20
#no span bpdufilter enable //disabling BPDU filter on port 20 of MT701
MT702 #show int status //we will see that the interface et ⅓ will be shown as error-disabled due to BPDU guard which disables it due to the broadcasts
#show int et ⅓ status error //we can see the reason for the error-disabled- shown as bpduguard
-------
|
MT704 #int et 19 #shutdown #no shutdown |
In another computer, MT704 #watch diff show span \\we can see how fast an port is changing from alternate to root and to original again
MT704 #watch diff show span detail \\we can the number of topology changes and the time |
In another computer, MT704 #tcpdump int et 20 |
------
MT701 #watch diff show mac add //we will see that only the mac addresses on designated ports are cleared. The mac addresses on root port are unaffected.
MT702 #int et1/1
#shut //we will see that the mac table on MT701 is cleared for the interface et 19 (since et 19 is connected to 1/1)
#no shut
-------
MT702 #int et ½
#span guard root
MT704 #span priority 0
//thus, now for MT702, it gets a superior BPDU to a root bridge MT704. But, already it thinks MT701 is the root bridge
MT702 #show span //it shows inconsistent state on et ½ since we have configured root guard. If we had not configured, then, this port would have become root port and MT704 would have become the root bridge.
-------
MT701 #int et23
#span fastport auto
MN431 #ping 10.1.10.2
|
In another computer first type this and watch, MT701 #logging console 7 #logging monitor debugging #terminal monitor //this command displays the debugging and changes on the monitor (no need to use show logging separately)
|
MT701 #int et 23 #shut #no shut
|
//we will see that in debugging, it takes around 20 seconds to move the port to listening port and then to designated port.
MT701 #int et23
#span fastport edge
& repeat the above steps // we will see that the moving only takes 1 second.
--------
ASSIGNMENT QUESTIONS:
Counting to Infinity http://blog.ine.com/wp-content/uploads/2011/11/understanding-stp-rstp-convergence.pdf
Proposal and Agreement
http://blog.ine.com/wp-content/uploads/2011/11/understanding-stp-rstp-convergence.pdf
4) Difference b/w STP and RSTP:
https://cciethebeginning.wordpress.com/2008/11/20/differences-between-stp-and-rstp/
CONTROL PLANE: